
Why Mobile Application Pentest Testing is Crucial
Protection Against Data Breaches:
Mobile apps often handle sensitive information such as personal data, financial details, and login credentials. Penetration testing helps ensure that this data is protected from unauthorized access and breaches.
Reputation Management:
A security breach can significantly damage your brand’s reputation. By proactively testing and securing your mobile applications, you demonstrate a commitment to protecting your users, thereby enhancing trust and loyalty.
Simulate Real-World Attacks:
By modeling real-world attacks, such as social engineering, you can gain an unbiased and comprehensive assessment of your company’s security posture. This approach helps to evaluate the effectiveness of your existing security mechanisms in practice, rather than just in theory.
Compliance and Regulation:
Many industries are governed by stringent regulatory requirements such as GDPR, HIPAA, and PCI-DSS. Regular pentesting ensures that your mobile applications meet these compliance standards, avoiding legal repercussions and penalties.
Improved App Performance:
Security vulnerabilities can often lead to performance issues. Addressing these weaknesses not only makes your app more secure but also enhances its overall functionality and user experience.
Avoid Business Disruptions:
Regular security assessments and network audits help prevent interruptions to business operations.
Our Mobile Application Pentest Testing Services
At Pentest Testing Services, we offer a thorough and systematic approach to mobile application penetration testing. Our services include:
1. Static Analysis:
Reviewing the app’s codebase to identify potential security vulnerabilities without executing the application. This includes analyzing the code for common security flaws such as insecure data storage, weak encryption, and code injection.
2. Dynamic Analysis:
Testing the running application to identify security vulnerabilities. This involves simulating attacks to understand how the app behaves under different conditions and uncovering issues such as authentication flaws, session management vulnerabilities, and insecure communication.
3. Reverse Engineering:
Analyzing the app’s binary code to understand its functionality and identify potential security weaknesses. This helps in uncovering hard-coded secrets, API keys, and other sensitive information that could be exploited.
4. Network Communication Analysis:
Evaluating the app’s network interactions to ensure that data transmitted over the network is secure. This includes checking for SSL/TLS vulnerabilities, man-in-the-middle attack risks, and data leakage during transmission.
5. Platform-Specific Testing:
Assessing the app’s interaction with the mobile platform (iOS, Android) to identify platform-specific vulnerabilities. This includes checking for improper use of platform APIs, insecure platform configurations, and potential exploit vectors.
6. Remediation Support:
Providing detailed reports and actionable recommendations to help you address identified vulnerabilities. Our experts work closely with your development team to ensure that all security issues are resolved effectively.
⭐ What Our Clients Say
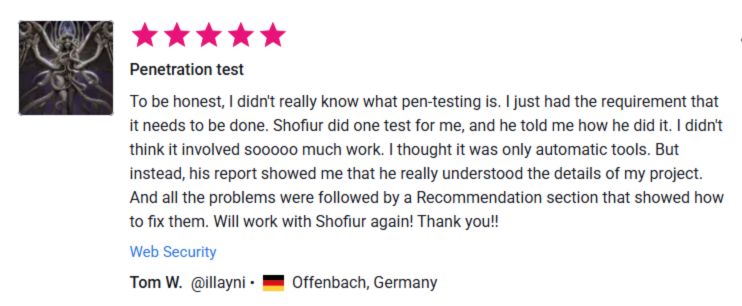

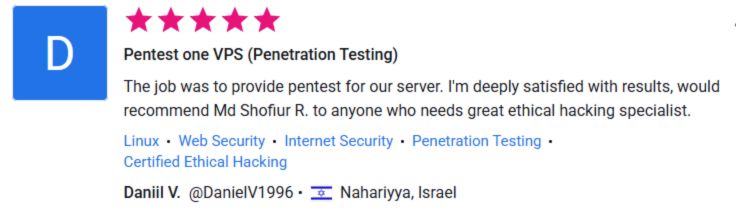
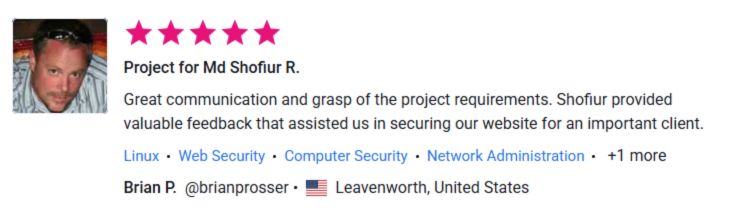
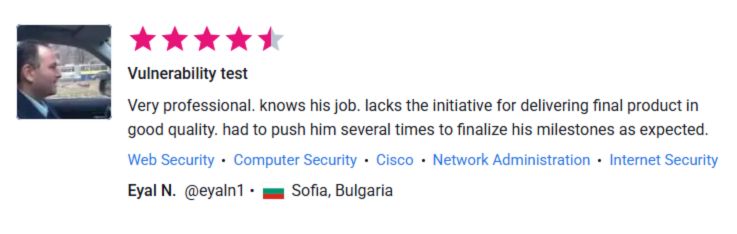
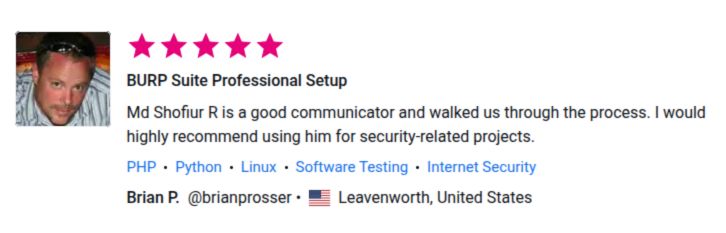
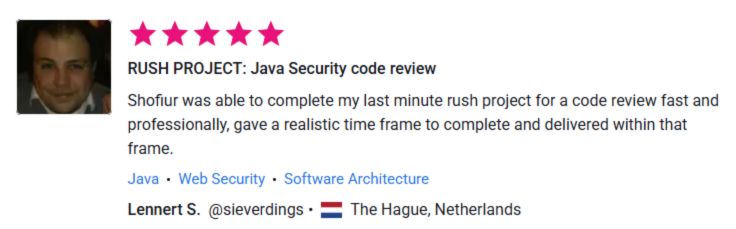
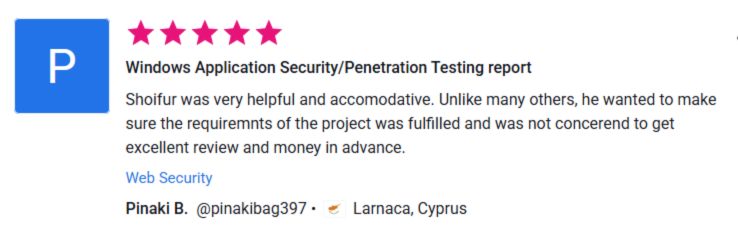
See More Client Results
Want to read more verified feedback and real-world outcomes from our engagements?
Explore our dedicated Testimonials page for detailed success stories across web, mobile, cloud, and AI app security.
Also, Securing AI-Driven Apps
Our team also offers end-to-end testing for AI-based applications. Learn more about how we secure ML models, APIs, and pipelines.
Enhance Your Cybersecurity Beyond Mobile Applications
While mobile application security is crucial, it’s just one piece of the puzzle. To ensure comprehensive protection across your entire digital ecosystem, consider exploring broader cybersecurity solutions. Our sister site, Cybersrely, offers a range of services including network security, vulnerability assessments, and more. Visit Cybersrely to discover how you can safeguard all aspects of your digital presence.
Want to resell or refer our services to your clients?
👉 Learn more about our Cybersecurity Agency Partnership Program
https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
Recent Case Studies
From vulnerability assessments to full-scale pentests — see how we deliver measurable impact.
Frequently Asked Questions
Find answers to commonly asked questions about our products and services.


